Traffic from 23.225.141.70 – or: About SYN-Floods and black holes
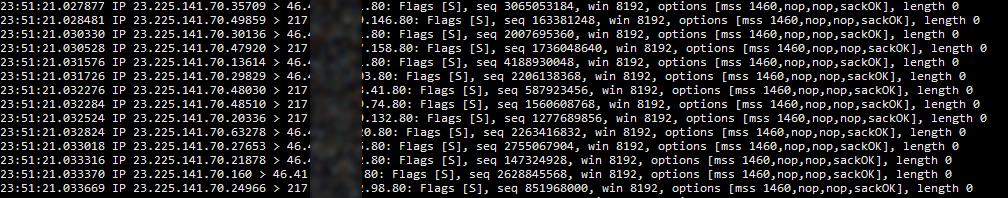
Yesterday (26th September, 2018) weird traffic originating from 23.225.141.70 caught my attention as it touched nearly every single one of my servers.
What was weird about the traffic: It's a SYN flood, targeting port 80/TCP on my servers.
After a quick duck test I'm sure:
- It looks like a SYN flood
- It feels like a SYN flood
- It has potential impact like a SYN flood
- It is a SYN flood!
Why are you attacking my system?! Hold on! It's neither an attack nor a SYN flood!
If it's not a SYN flood - what IS it?
Spoiler alert: It's not a SYN flood! Actually, it's a sneaky DDoS attack against 23.225.141.70.
Background:
A TCP connection is opened by a handshake. With that, the client sends a TCP SYN packet towards the server it wants to reach.
This server answers with SYN-ACK, the client answers again with ACK - and then you eventually have an open TCP connection and can transmit data.
But: If there is no answer on the server's SYN-ACK, the server sends its packet again, like TCP always does with lost packets. And sends it again. Aaaand again.
Depending on operating system and configuration a server normally repeats a SYN-ACK packet 3 to 5 times until it's giving up.
So, if an attacker sends TCP SYN packets with a spoofed source address (the address of the victim) to a server on the internet, the server will
respond to this single packet with five SYN-ACK packets.
Or, in other words: If someone sends 100k SYN packets to open ports on random servers, that would generate about 500k SYN-ACK packets sent towards the victim.
With very high packet rates, the victim is literally blown out of the internet. With a packet rate high enough, you will not only overwhelm the victim's server with
packets - you might also reach the network equipments forwarding capacities and therefore disrupt connectivity of the whole destination network.
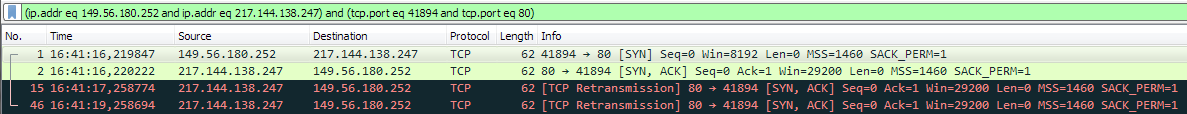 This is a screenshot of wireshark at a similar SYN-ACK flood event (therefore with other IP addresses), captured on one of my servers. It shows a SYN packet coming from 149.56.180.252 to my server - and my server responds three times bevore giving up.
This is a screenshot of wireshark at a similar SYN-ACK flood event (therefore with other IP addresses), captured on one of my servers. It shows a SYN packet coming from 149.56.180.252 to my server - and my server responds three times bevore giving up.
Since TCP services are commonly used in the internet and nearly every server has at least one open TCP port, these can be misused by attackers for this purpose.
On one of our core routers I mirrored traffic from this IP address – and I was really impressed:
Hundreds of SYN packets per second to hundreds of IP addresses on our network! I assume our network generated SYN-ACKs at a rate of at least a thousand packets per second.
The black hole
When I was looking deeper into this, all of those SYN-ACKs were already discarded by our core routers –
because of a blackhole routing advertisement.
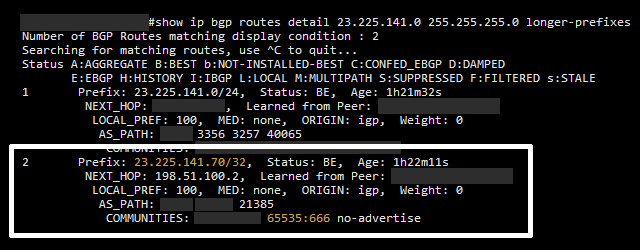
A blackhole route is a BGP route for a single IPv4 address, flagged with the special BGP community 65535:666 (the orange text on the bottom), advertised into the world.
Those special routes are translated into a local nullroute on most provider and carrier routers – like we do.
The effect of this is pretty impressive: Traffic towards the blackholed IP address is discarded on most routers and therefore this DDoS traffic is not reaching your network.
The target of the attack is offline due to blackholing (and therefore the goal of the attack is reached), but at least the rest of your network is not affected by the attack.
So, with seeing this blackhole route, I'm very sure, the owner of this particular IP address indicates no interest in receiving those SYN-ACKs. ;-)
And as long as this blackhole route is present, he will not get any of those packets.
But, of course, incoming SYN packets are still arriving and, of course, the targetet servers in our network will still reply to these SYN packets.
Of course, our router will eat the outgoing SYN-ACK packets - but for some special systems (i.e. IoT devices) this unusual huge DDoS attack feels like a SYN flood.